A Five-Part Blog Series to Bust the Myths Surrounding VPN Intelligence Data
In this five-part blog series, we tackle the questions our customers ask us, with a goal of busting the myths that are driving those questions. In our first blog post of the series, we dispelled the myth that all VPN-driven data is the same. For Part Two, we addressed the myth that VPN breadth doesn’t matter. Part Three dispelled the myth that IT teams only need to worry about detecting the VPN services included in a Top Ten list they’ve found online.
This blog post, the fourth in our series, tackles a pernicious myth that VPN threat vectors originate from common sources and remain static.
Myth #4: VPN threat vectors originate from common sources and remain static.
There are many reasons why this statement is false. Before we can even begin to identify the IP addresses that are proxies, we need to understand how the IP address space operates. There are three portions of the routable IP space that apply in this context:
- ISP blocks, which are tied to ISPs that offer home and business connectivity
- Mobile blocks, which are for mobile and IoT devices and provided by telecom companies
- Hosting IP blocks, which is where VPN activity originated and continues to live, services all kinds of connectivity needs, such as domain or web hosting, co-location, and so on.
However, over the past 10 years, VPN providers have begun to tap into IP addresses that historically have been within Hosted IP address blocks to dynamic addresses within the ISP and Mobile blocks and are starting to leverage those as proxies.
Dynamic vs Static IPs
Given the distinction in the routable IP space, it’s no surprise that there are two broad classes of IP addresses: static and dynamic.
- Static IP Address. A static IP address is one that has consistent geolocation, meaning at the time it is analyzed its geolocation is the same as previously identified. Static IP addresses are likely tied to the same end users if within an ISP block.
- Dynamic IP Address. A dynamic IP address is one whose geolocation changes frequently. It’s dynamic because it can service different end users at any given moment. This is more common in Mobile and ISP blocks because end users fluctuate within a given area. These addresses are difficult to block as the end user may be different every day making blocking the IP address problematic.
Example of a Dynamic IP Address
A home user’s IP address, also known as a residential IP address, is a highly valuable IP address to a VPN provider as they are dynamic and can change everyday. A VPN service will use these addresses for their service, knowing that the IP address can change at any given moment, making it easier to circumvent restrictions that would apply to Static IP addresses.
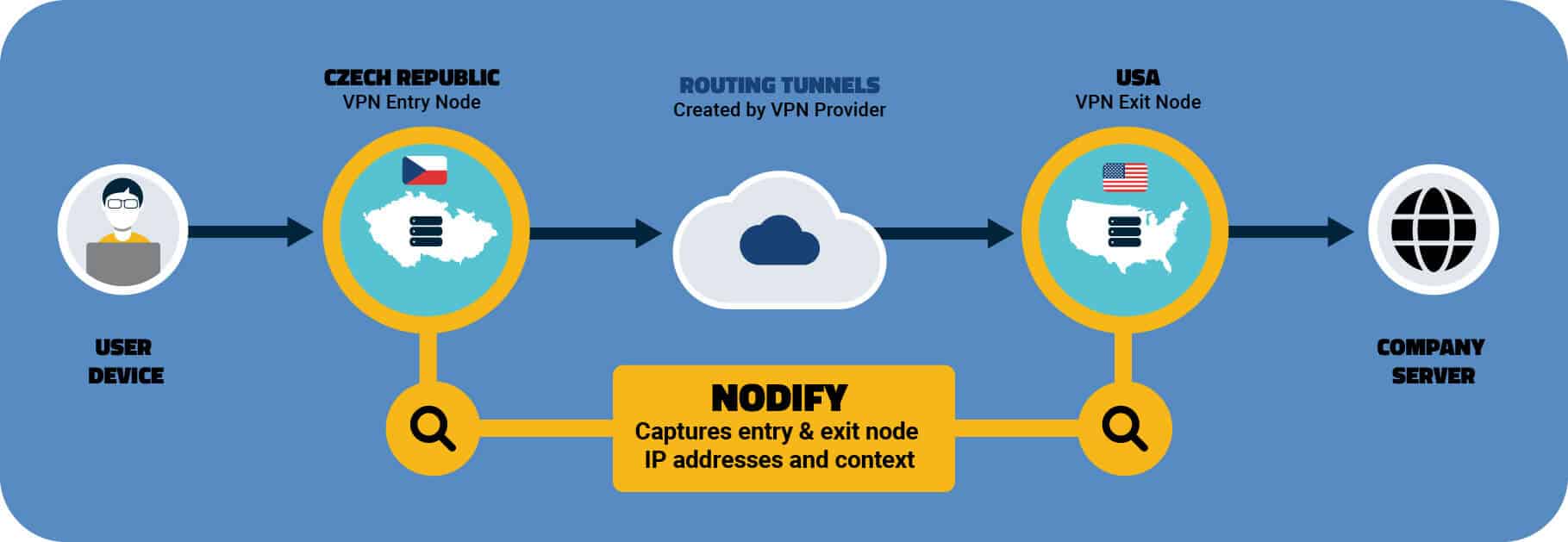
Example of How VPN Exit Nodes Operate
Lets say a user signs up for “Big Name” VPN user and connects to a server in the U.K. They will be assigned a Static IP address of “1.2.3.4” from a hosting provider like “Digital Ocean”. That is the entrance node. The “Big Name” VPN user then wants to visit a streaming media provider. At that point the provider routes the user through an additional IP address “5.6.7.8” from an ISP like “British Telecom”. This is the exit node. And this is the IP address that looks like a residential IP address.
Furthermore, if the “Big Name” VPN user leaves the U.K. server and chooses a U.S. server from the “Big Name” VPN provider, that IP address is “9.10.11.12” and it belongs to a hosting provider, such as “Linode LLC”. This is the entrance node. If the user connects to a media streaming service, they get routed through “13.14.15.16 ” which belongs to an ISP “Comcast Cable”. This is the exit node and this is also another residential IP address.
It’s also a good example of the challenges it poses to companies that offer services to that user. Once upon a time, security teams could reasonably assume that an IP address associated with a proxy was a bad actor who should be blocked from accessing their networks or services or a bot performing a malicious action. But we see in this example that a home user can be associated with a proxy. If you’re a streaming media company, do you still block this home user, who may be a paying customer?
The Bottom Line
What does this mean for security teams? You can identify an IP address as a threat vector and block it, but that is no assurance that you’ve stopped the bad actor. That actor can simply access and use another IP address to attack your network. This is when the process of blocking certain entities can begin to look like a game of whack-a-mole.
The Digital Element Difference:
We deploy multiple strategies to help security professionals to stay on top of threat vectors.
First, we identify which IP blocks are static and which are dynamic using proprietary methodologies. Additionally, we use several different applications, each with its own methodology, to identify the IP addresses that are currently being used as proxies.
Importantly, we also see the volume and frequency of both static and dynamic IP addresses that are tied to VPNs. We can verify that dynamic IPs tied to VPNs remain predominantly in the Hosting space, even as VPN providers are actively moving into static IP space.
Given the dynamic nature of the space, we also have a very robust aging mechanism to ensure that we don’t label an IP address as a proxy longer than we should. This aging mechanism also runs 24/7.
Up Next: In our fifth and final myth of this series, we’ll talk about the pitfalls of relying only on geolocation datasets, and explain why blocking an entire geographic region isn’t always in your best interest.