A Five-Part Blog Series to Bust the Myths Surrounding VPN Intelligence Data
Over the past few months, we’ve addressed the common questions we hear most frequently when speaking to customers about the rise of VPNs. In our discussions we hear a lot of myths about VPNs — myths that if believed can put corporation information and networks at risk.
To date, we’ve addressed the following myths:
- All VPN-data driven data is the same
- VPN breadth does matter
- IT teams only need to concern themselves with VPNs listed in popular Top Ten lists
- VPN threat vectors originate from common sources and remain static
In this final post in the series, we take on the myth that country-level IP geo data provides sufficient protection.
Myth #5: Country-level IP geo provides sufficient protection.
Throughout this blog post series, we’ve highlighted just how easy it is for VPN users to change their IP address to one that appears to originate from another location. In fact, this feature is so ubiquitous and easy that it is positioned as a selling point by VPNs that sell to consumers.
In a blog post, vpnMentor shows readers how to change their region in seconds. vpnMentor is owned by Kape Technologies PLC, which owns the following products: ExpressVPN, CyberGhost, ZenMate, Private Internet Access, and Intego (which speaks to blog number 3 in this series, Covering the Top 10 VPN Services is Sufficient).

This begs the question: how much should you trust an IP location as a proxy for a legitimate user? Let’s say a company has a policy to block all IP addresses that originate in Russia or Iran for security purposes. But does this policy actually provide any protection for the company? The answer is no, given how easy it is to change one’s IP address geographic location.
Conversely, there are good and bad VPN providers and users in every country, including the U.S. If you block users on a country level, you may inadvertently block legitimate users, some of whom may be your own employees or customers.
Let’s say an R&D company blocks IP addresses that originate in Iran. All traffic coming from that country would be deemed nefarious, right? But what if that company sent a team of scientists to present a paper to the International Conference on Science Technology and Management, which will take place in Tehran? The company’s scientists would be prevented from exchanging email with their colleagues back at home.
It’s All About Context
Here’s the reality: IP address data alone won’t protect your corporate network, but it will provide substantial context about incoming traffic. From there you can make intelligent decisions, and establish best practices, as to how to treat VPN traffic.
For instance, some VPNs offer features that are friendly to criminals, such as payment via untraceable crypto currencies, no logging which enable them to cover their tracks. If a crime against your network occurs, such VPNs will not assist you or law enforcement in tracking down the perpetrators.
Other VPNs tout the fact that users can easily change their IP address in order to bypass digital rights access restrictions, as the above example illustrates.
You may not want users of such VPNs to access your network, regardless of where they reside. In fact, you establish a set of best practices that bar users from your network based on the VPN service they use. But to implement such rules, you’ll need access to that rich contextual data in order to set access rules for your network.
The Digital Element Difference
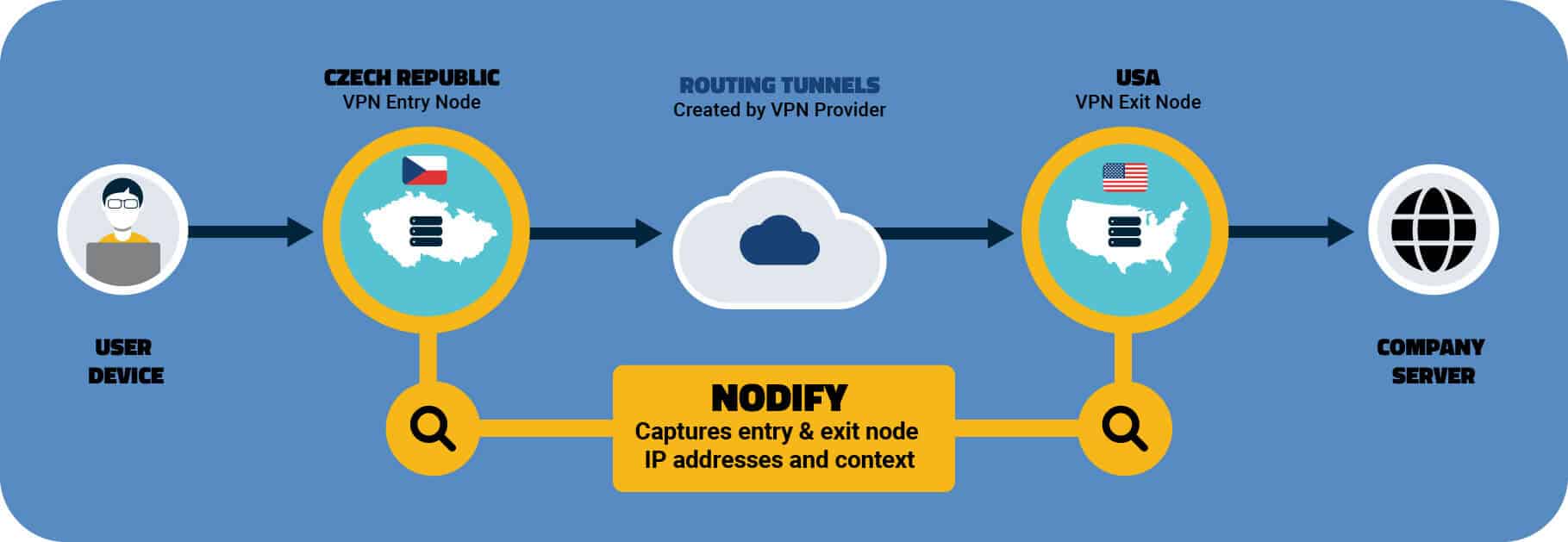
Digital Element’s Nodify provides a rich set of IP address intelligence data so that you can understand the context of users who access your network, including:
- VPN classification
- Provider’s name/URL
- Distinction between residential or commercial
- IP addresses related to a provider
With this data in hand, you can make smart decisions about the VPN traffic that accesses your network, and set rules to enforce it. For instance, you can opt to flag all commercial VPN traffic with additional multi-factor authentication automatically.
To learn more about VPNs and how to incorporate IP geolocation and intelligence data for corporate network protection, download our white paper “The Need for Proxy/VPN Data in Today’s Heightened Cybersecurity State.”