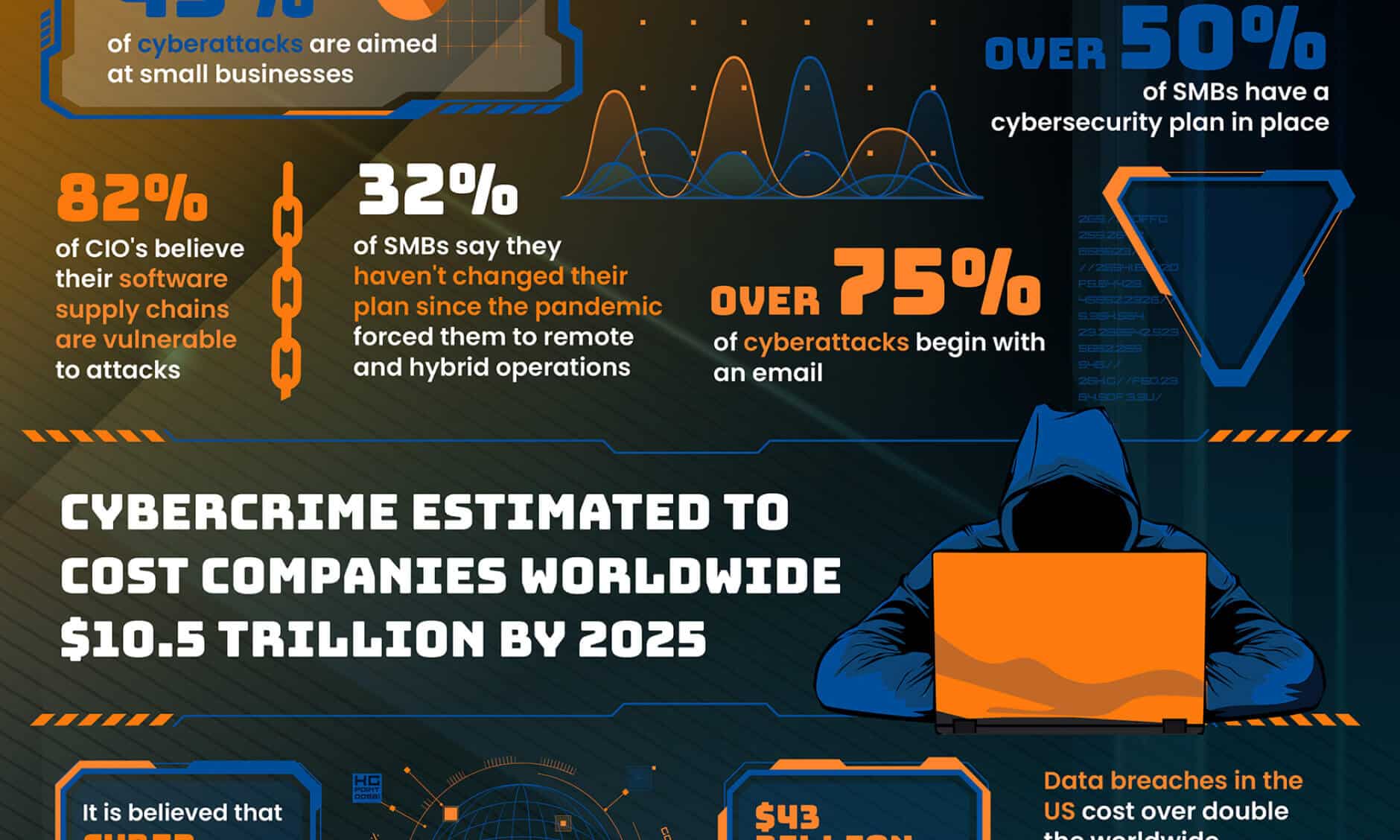
IP geolocation is a subject that is often misunderstood. Generally people understand that it is about mapping of IP addresses of internet-connected devices to their geographic location, but the nuances behind accuracy, coverage, and granularity can be a bit, well…confusing.
In this post, we’ll break down some of the intricacies of IP geolocation and share some facts and examples that will clear up some of the confusion, and demonstrate how corporate security and marketing teams can receive unmatched data refined by experience and an unending commitment to data quality.
The Importance of Bi-directional Accuracy
Let’s start by saying you’re a marketer and you want to target Atlanta, GA, USA as a market in a campaign you are running. As an ever-prudent marketer, would your intention be to target the city center of Atlanta (Atlanta Proper) and the IP addresses associated with that location? Or, would you expand the geographic focus to include the suburbs, and subsequently, the majority of what is considered the population of Atlanta?
We’re pretty sure it’s safe to assume it’s the latter. As you know, urban sprawl continues to rise, changing the population densities and demographic makeup within cities and in neighboring towns.
Digital Element has accounted for how this trend affects IP geo data, and we’ve gone great lengths to make investments in our technology to help corporate marketing teams and their agencies ensure bi-directional accuracy of IP geo on a meaningful level. What does that mean for marketers?
More is Less
Back to the Atlanta example: let’s say Digital Element provides a marketer with 5.8 million IP addresses for the Atlanta market. Another IP address provider may return almost 6.5 million IP addresses for the same market – a pretty substantial difference, right?
Here’s where the science gets a bit tricky.
At first glance, it may seem like 6.5 million is a more valuable data set. But digging in a little deeper, all of the IPs provided are associated with the city of Atlanta. And, if we do a quick Google search it’s apparent that the population of Atlanta (proper) is just under 500,000. So, where are those other 6 million IP addresses located?
And, how can marketers be confident that they’re accurately targeting the Atlanta metropolitan market if they have no visibility into where the other IP addresses actually are? The short answer is: they can’t. And, hint: this is how IP address databases can be misrepresented and potentially inflated.
In this situation, more is less (accurate).
So what about Digital Element’s 5.8 million IP addresses? The total number may be less, but that is due to good reason: Digital Element maps the IP addresses to their correct geographic locations. This can be further validated by population figures when dissecting the data. Only a small portion of the 5.8 million IP addresses would indicate they are coming from Atlanta proper, and the rest would fall into identifiable adjacent cities.
How does Digital Element do it? Digital Element leverages truth set data from GPS coordinates from mobile devices to validate the location of IP addresses. Put simply, Digital Element receives the latitude and longitude of an IP address when we “observe” a device connecting to the internet using that IP address, and use that to verify the general IP vicinity data Digital Element returns to clients. We can then confirm that an IP address is in a specific city based on the lat/long info received when a device is using that IP address.
Digital Element does this a lot. In fact, Digital Element receives over 950 billion observations from over 1.5 billion devices on a monthly basis. This allows us to section the world into useful geographic segments, no matter how small the city or suburb. Digital Element is the only IP geolocation provider that can do this at scale.
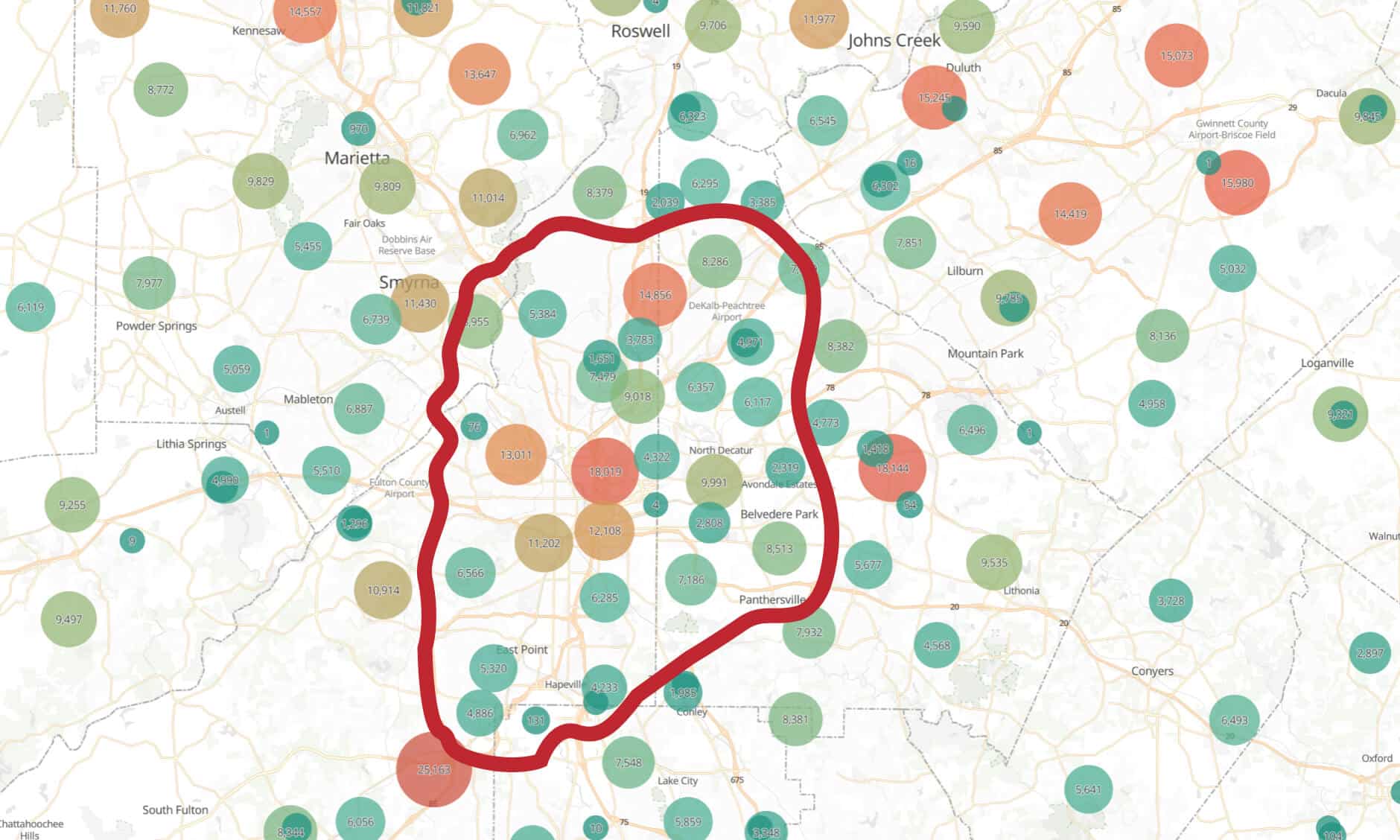
The red color bubbles are the larger number of IPs at the given location. As you can see in the bottom left corner of Atlanta, the red bubble is for the Atlanta Airport, which has multiple network blocks of IPs allocated to it. However, you can also see red bubbles generally on the northside of Atlanta, which is where a larger portion of the metro Atlanta population resides.
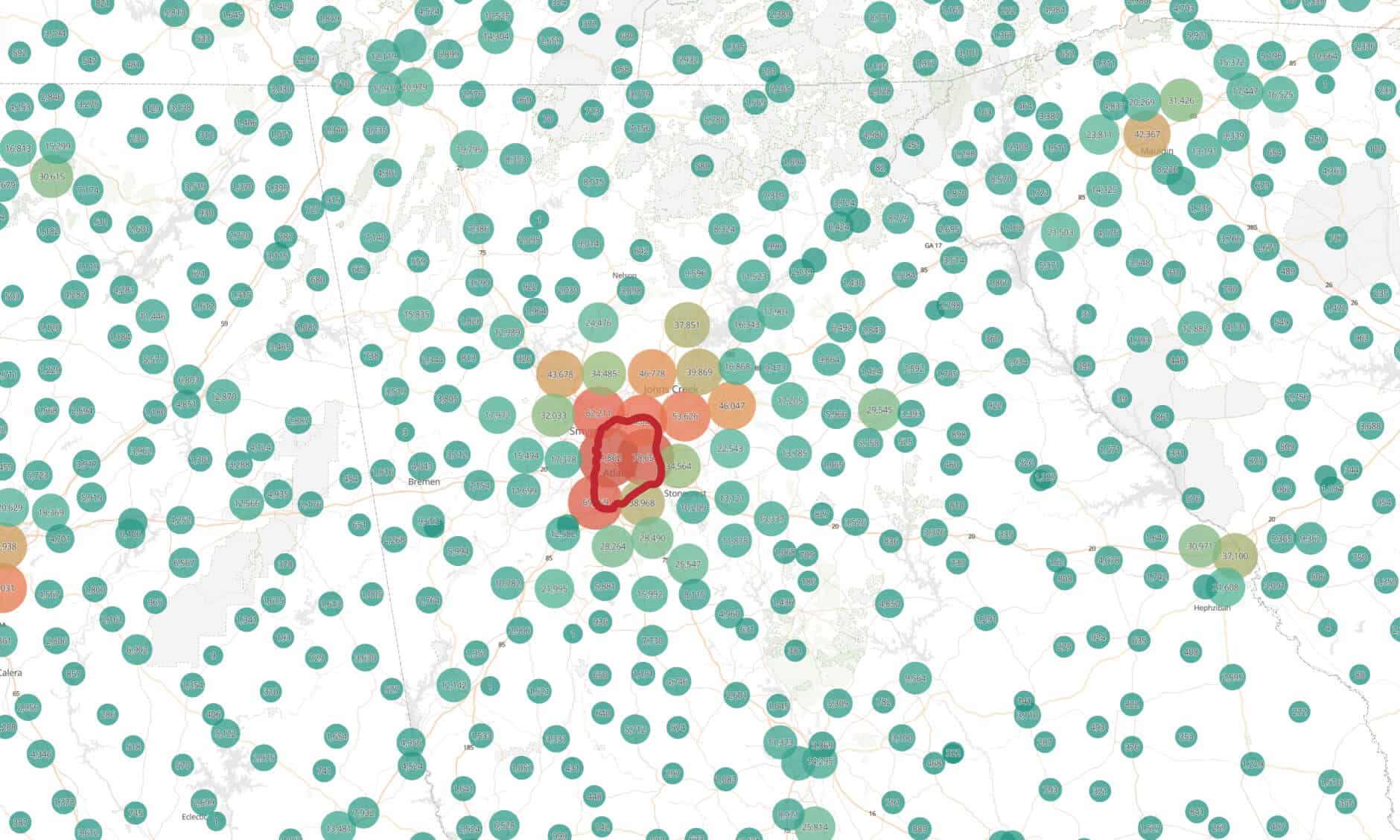
When zooming out further to show the region where Atlanta is located, you can see how the IPs correctly represent the rural areas and the more densely populated areas, not the center of the city of Atlanta.
In comparison, a city such as Tokyo has a denser population that reaches further out than the city center. This again is representative of the IPs associated with those areas in this map of Tokyo, overlaid with IPs associated with those areas.
To wrap up, Digital Element provides unparalleled bi-directional coverage for cities and postcodes. We cover them as they were set up by the local government, and map the IP addresses that belong to each.
This is the reason why Digital Element is able to map over 4 million locations (cities and postal codes) in the world, which is an order of magnitude higher than any other provider in this space. For Digital Element customers, this translates into enhanced accuracy, better insights, and greater performance.
Challenges of IP Stability
Another issue that is misunderstood is the fact that IP addresses are not static, and therefore mapping alone can be unreliable. For example, two IP geolocation providers may place an IP address as the same location, but if neither can validate that an IP address was recently “observed” at that location, only relative confidence can be had. Here is why.
Sourcing accurate IP addresses geolocation is not a perfect science. Compounding the fact that it is hard to do, is the fact that it needs to be done often–like, daily basis often.
Because Digital Element sources data from over 750 million mobile devices in a given thirty-day period, and confirms the location of IP addresses using the lat/long provided by the mobile devices, we are able to provide greater confidence as it relates to the actual IP address location.
So, when two companies are matching on an IP address, the physical location provided matters, but nearly equally as important is the last date that IP address was observed, as it is the last confirmed location of that IP address. This is another core competency of Digital Element.
With that said, despite Digital Element’s unique ability to confirm IP address locations, there are still challenges in ensuring accurate location of IP addresses. To address this, Digital Element layers on proprietary methodologies to further validate data and then filter it in order to provide the highest IP address geolocation accuracy available.
Because Digital Element leverages the largest number of datasets in the space, we’re able to contextualize IP address data, therefore helping companies remove useless IP addresses linked to VPNs, cell towers or proxies, that are often erroneously included.
Finally, everything outlined above is underscored by Digital Element’s privacy-centric culture, enabling clients to confidently leverage data to meet the needs of their business. From campaign optimization in AdTech, to threat prevention in Cyber Security, Digital Element takes pride in our ability to provide IP geolocation with the most useful accuracy while leveraging the latest technology to support an evolving landscape.
IP geolocation is an easily misunderstood subject, but one that Digital Element is passionate about “decoding” to bring clarity to security and marketing teams who rely on that data, and validate Digital Element’s unique ability to provide the level of data needed to positively impact your business.
To learn how IP geolocation data can be used across multiple industries, contact us or visit our Use Cases page.