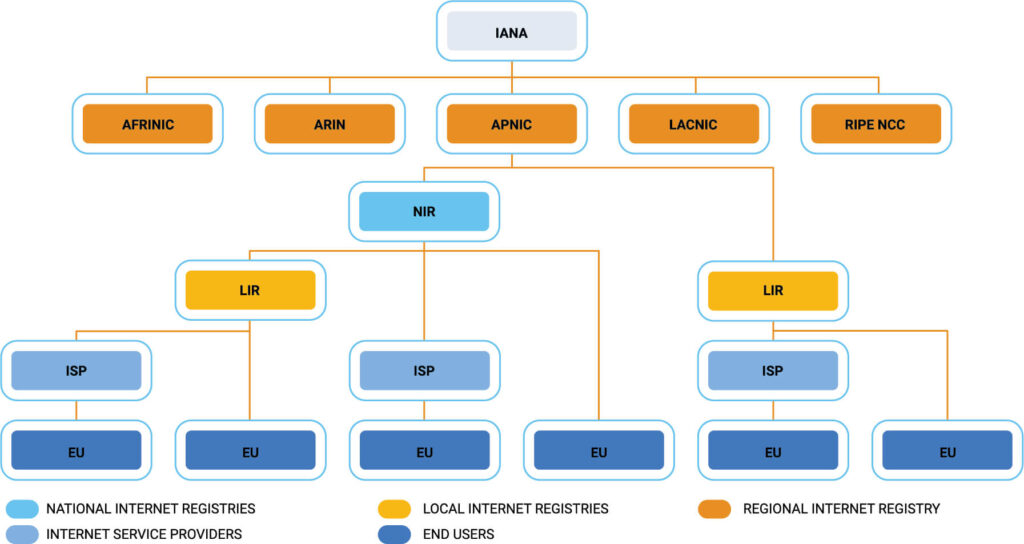
According to recent data analyzed by Digital Element, a single data breach costs the average company by $9.44 million in the US. But if a company can contain that same data breach within the first 200 days, it can save an average of $1.12 million in damages.
Cybersecurity solutions, such as IP geolocation and VPN identification, can help your business protect the integrity of your network, systems, and data. But how do you evaluate a cybersecurity solution to decide if it’s right for your organization?
In this guide, we’ll break down everything you need to know about the cybersecurity landscape. We’ll talk about everything from IP location to firewall applications to IoT security — helping you dissect the uses of each in protecting your business data and systems.
What are cybersecurity solutions?
Cybersecurity solutions are a collection of methods, technologies, and practices designed to protect digital systems, networks, and data from various forms of cyber threats. These threats can range from ransomware, viruses, and malware to sophisticated cyber-attacks aimed at harming digital infrastructure.
At a high level, cybersecurity solutions use automation to safeguard digital assets. This involves ensuring the confidentiality, integrity, and availability of data for both businesses and individuals:
- Confidentiality means that data is accessible only to authorized individuals.
- Integrity ensures that the data is accurate and hasn’t been tampered with.
- Availability ensures that data and services are accessible when needed.
The cybersecurity solutions industry is vast and dynamic, continually evolving to keep up with the changing threat landscape. As new types of threats emerge, the industry develops new solutions to counter them.
This constant evolution makes the cybersecurity industry a critical component of the modern digital economy. It’s an industry that not only protects businesses and individuals but also enables them to operate with confidence in the digital world.
Importance of cybersecurity solutions
Security solutions play a critical role in combating digital threats by providing a multi-layered defense mechanism that safeguards networks, systems, and data from every type of cybercriminal. Here’s a more detailed breakdown of their role:
- Prevention: The first line of defense in any cybersecurity strategy is prevention. Cybersecurity solutions, such as antivirus software, firewalls, and intrusion prevention systems, are designed to prevent threats from penetrating networks and systems.
- Detection: Despite the best prevention efforts, some threats may still manage to infiltrate systems. This is where detection comes in. Cybersecurity solutions like intrusion detection systems (IDS) and security information and event management (SIEM) systems monitor networks and systems for unusual activity that could indicate a security breach.
- Response: Once you detect a threat, it’s crucial to respond quickly to minimize damage. Cybersecurity solutions can automate certain response actions, such as isolating infected systems to prevent the spread of malware or blocking IP addresses that are the source of an attack.
- Recovery: After a cyberattack, cybersecurity solutions play a key role in remediation and recovery efforts. This can involve removing malware from systems, restoring systems and data from backups, and patching vulnerabilities to prevent future attacks.
- Education: Cybersecurity solutions also include training and awareness platforms. These tools educate users about potential threats, such as phishing emails or malicious websites, and teach them how to avoid falling victim to these threats.
In-depth look at different cybersecurity solutions
Businesses, big and small, are increasingly reliant on online platforms and digital technologies. While this digital transformation has opened up a world of opportunities, it has also exposed businesses to a new world of threats from hackers.
Cyberattacks are no longer a matter of ‘if’ but ‘when’. From sneaky malware slipping through the cracks to large-scale data breaches, digital threats are real and can cause serious damage. The fallout isn’t just about losing data—it can lead to financial loss, damage to reputation, and shaken trust from customers and partners.
Here’s an overview of the different types of cybersecurity services that have emerged to combat this growing security threat, from IP geolocation to encryption tools to IoT security:
IP geolocation
IP geolocation is a cybersecurity solution that identifies the geographical location of an Internet-connected device using its IP address. This technology is crucial in detecting and mitigating potential threats based on geographic anomalies.
Key features
- Location Identification: It can pinpoint the geographic location of a device, down to the post code level, providing valuable context about user behavior and potential threats.
- Geo-blocking: It allows or denies access to content or services based on the user’s location, helping businesses comply with regional regulations and licensing agreements.
- Threat Intelligence: It identifies potential threats based on geographic patterns, such as a sudden surge in traffic from a specific location.
Benefits
- Enhanced security: By identifying unusual or suspicious locations, businesses can detect potential cyber threats and take preventive action.
- Regulatory compliance: Geo-blocking helps businesses comply with regional regulations and licensing agreements.
- Improved user experience: Businesses can customize content and services based on the user’s location, improving the user experience.
Antivirus software
Antivirus software is a fundamental security tool designed to detect, prevent, and remove malware, including viruses, worms, and trojans, from computers and network systems.
Key features
- Real-time scanning: It continuously checks all files and programs on a computer or network for malware, providing ongoing protection.
- Virus definition updates: It regularly updates its database of virus definitions, enabling it to recognize and combat new threats.
- Automatic cleaning: Upon detecting malware, it automatically removes or quarantines it to prevent further harm.
Benefits
- Device and application security: It provides a crucial line of defense against a wide range of malware, keeping devices and applications safe.
- Data security: By preventing malware infections, it helps protect sensitive data from theft or corruption.
- Peace of mind: Users can browse the internet and download files with confidence, knowing that their antivirus software is protecting them.
Firewalls
Firewalls serve as a gatekeeper for networks, controlling incoming and outgoing network traffic based on predetermined security rules and blocking unauthorized access. They’re crucial to both on-premises and cloud security.
Key features
- Traffic control: It regulates network traffic based on security rules, allowing or blocking specific types of traffic.
- Intrusion prevention: It blocks unauthorized access attempts, preventing intruders from gaining access to the network.
- VPN support: Many firewalls support Virtual Private Networks (VPNs), allowing secure remote access to the network.
Benefits
- Network protection: It shields internal networks from external threats, providing a fundamental layer of security for any network.
- Enhanced privacy: By controlling outbound traffic, it prevents unauthorized transmission of data from the network, protecting user privacy.
- Controlled access: It allows businesses to control which services and applications can send or receive data over the network, reducing the potential attack surface.
Encryption tools
Encryption tools use complex algorithms to convert readable data into a coded form, preventing unauthorized access to the data.
Key features
- Data encryption: It transforms readable data (plaintext) into coded form (ciphertext), ensuring that even if malicious actors intercept the data, it cannot be understood without the decryption key.
- Secure key management: It provides mechanisms for securely generating, distributing, storing, and retiring encryption keys.
- File and disk encryption: It allows specific files or entire storage devices to be encrypted, protecting data at rest.
Benefits
- Data protection: It provides a high level of security for sensitive data, ensuring that only authorized parties can access it.
- Compliance: Many regulations require data to be encrypted, so encryption tools help businesses comply with these requirements.
- Confidentiality: It ensures the confidentiality of data during transmission and storage, protecting it from unauthorized access.
Network security
Network security involves a range of practices and technologies designed to protect the usability, reliability, integrity, and safety of a network and its associated data.
Key features
- Access control: It regulates who can access the network and what they can do, based on user profiles, roles, and policies.
- Intrusion Detection Systems (IDS): It monitors network traffic for suspicious activity and alerts administrators to potential security incidents.
- Security policy enforcement: It enforces rules governing network use, such as password policies and acceptable use policies.
Benefits
- Protection from attacks: It defends the network against a wide range of threats, including hacking attempts, malware, and denial of service (DoS) attacks.
- Data integrity: By preventing unauthorized access and modification of data, it ensures the integrity of data on the network.
- Business continuity: By protecting the network infrastructure, it ensures that network services remain available, supporting business continuity.
Endpoint security
Endpoint security is a strategy where businesses manage network security at individual access points, such as laptops, smartphones, or desktops, rather than at the network level.
Key features
- Device protection: It secures each endpoint device on a network, preventing threats from gaining a foothold on the network via vulnerable devices.
- Threat detection: It identifies and blocks potential threats at the endpoint level before they can spread to other parts of the network.
- Centralized management: It allows you to control all endpoint security measures from a single point, simplifying administration and ensuring consistent security policies.
Benefits
- Comprehensive protection: By securing all network entry points, it provides comprehensive network protection.
- Remote work security: It protects devices outside the traditional network perimeter, making it ideal for businesses with remote workers.
- Rapid response: By identifying and neutralizing threats at the endpoint level, it enables rapid response to security incidents.
IoT security
IoT security involves safeguarding internet-connected devices and networks in the Internet of Things (IoT), which can range from smart home devices to industrial control systems.
Key features
- Device authentication: It verifies the identity of IoT devices, preventing unauthorized devices from joining the network.
- Data encryption: It protects data transmitted between IoT devices, preventing eavesdropping and data theft.
- Regular updates: It ensures devices receive regular security updates, protecting them against known vulnerabilities.
Benefits
- Device security: It protects a wide range of IoT devices, which often lack the built-in security measures found in traditional IT devices.
- Data privacy: It ensures the sensitive data collected by IoT devices is secure, protecting user privacy.
- Network protection: By securing IoT devices, it prevents them from becoming points of intrusion into the network.
How to choose the right cybersecurity solution
Choosing the right cybersecurity solution is a critical decision that can significantly impact a business’s resilience against cyber threats. Here are some key factors to consider and common pitfalls to avoid during the selection process:
Factors to consider when selecting cybersecurity solutions
- Size of the business: The size of your business can influence the type and scale of cybersecurity solutions you need. Larger businesses may require more comprehensive solutions, while smaller businesses may need more cost-effective, scalable options.
- Industry-specific needs: Different industries face different types of threats and have different regulatory requirements. For example, a healthcare organization must comply with HIPAA regulations, which require specific data protection measures.
- Financial budget: Cybersecurity solutions can range in cost, and it’s important to find a solution that fits your budget but doesn’t compromise on essential features.
- Existing IT infrastructure: The cybersecurity solutions you choose should be compatible with your existing IT infrastructure. Consider the systems and software you’re already using and how a potential solution will integrate with them.
- Type of data: The sensitivity and type of data you handle can also influence your choice. If you handle sensitive customer data, robust encryption, and data protection measures are crucial.
- Future growth: Consider your business’s future growth and how that might impact your cybersecurity needs. Choose a solution that can scale with your business.
Common pitfalls to avoid with cybersecurity solutions
- Overlooking employee training: Human error can undermine even the best cybersecurity solutions. Don’t overlook the importance of employee training in cybersecurity best practices.
- Ignoring mobile security: With the rise of remote work, mobile devices are increasingly being used for business purposes. Ensure your cybersecurity solution covers mobile device security.
- Failing to plan for incident response: It’s not enough to just prevent cyber threats; you also need a plan for how to respond if a breach occurs. Look for solutions that include incident response capabilities.
- Choosing based on price alone: While budget is a factor, the cheapest solution may not provide the protection you need. Consider the potential cost of a data breach when deciding how much to invest in cybersecurity.
- Neglecting regular updates and maintenance: Cybersecurity is not a set-it-and-forget-it solution. Regular updates and maintenance are crucial to protect against new threats.
Unlock the power of cybersecurity through threat intelligence with Digital Element
We’ve journeyed through the ins and outs of cybersecurity solutions, explored what to consider when choosing one, and even tackled some common traps to avoid.
Whether it’s ad targeting, analytics, or fraud and security applications, it’s important for businesses to get the most returns from their digital infrastructure while staying on top of advanced cybersecurity threats.
For over 20 years, Digital element has provided top-notch IP geolocation solutions to businesses across the globe.
If you’re ready to level up your cybersecurity game, check out Digital Element and our complete list of Cybersecurity Solutions.